It’s essential these days to secure your computer and your internet activity. There are a variety of methods available now to make it very difficult for hackers to get onto your computer, such as firewalls and anti-malware programs. Encryption secures internet connections, even over WiFi networks.
Privacy is another matter. Even if a snooper is locked out from the contents of your communications by encryption, there is still plenty of information that your internet traffic gives away about you. Government agencies, Internet Service Providers (ISPs), marketing companies, and network owners are all able to see where you are and which sites you are communicating with.
You might think that it’s no big deal if others can see your activity on the internet, just as long as they can’t read your emails, or break into your conversations, or steal your credit card information. However, if someone is in hiding, such as a spy, a whistleblower, or a victim of domestic abuse, revealing location information can be fatal.
Both Tor and Virtual Private Networks (VPNs) employ methods that enhance the security offered by encryption to create privacy and near-anonymity. In this report, you will find out what each of these systems does, and which is better for creating privacy.
What is Tor?
The Tor system evolved from research carried out at US Naval Research Laboratory in the mid-1990s. This research looked into a way to mask communications locations and it created the concept of “the onion router.” Thus, when the researchers had found a viable method of creating privacy on the internet, it was referred to as the TOR project.
When the research institute set up a department to produce an implementation of the system, the name was transformed into the Tor Project. Today, the system is a protocol and open source software, managed by a not-for-profit company, called The Tor Project, Inc, which refers to the system as “Tor” rather than “TOR.”
 Tor-protected traffic still travels across the internet, but its routing information is obscured by repeated encryption. Each waypoint on the journey is managed by a node. A node on the path of a Tor journey is called a relay, and the point of exit from the network is called the exit node.
Tor-protected traffic still travels across the internet, but its routing information is obscured by repeated encryption. Each waypoint on the journey is managed by a node. A node on the path of a Tor journey is called a relay, and the point of exit from the network is called the exit node.
Each node in the journey decrypts a layer of encryption to discover the address of the next point in the chain to which it should pass the message on to. It received the package from somewhere and it knows where it came from. Thus, each node is only able to know the addresses of previous and next nodes in the chain. Only the first node knows the address of the source of the packet and only the endpoint knows the destination Internet Protocol (IP) address. Each node is created by an individual volunteer who makes disk space and internet bandwidth available to the community free of charge.
What is a Virtual Private Network?
A network that is laid out with cables within a business’s premises is called a local area network (LAN). The owner of the LAN can take steps to ensure that no one from outside the company is able to get access to the data on that network. When the company connects the LAN to the internet, that level of control is lost.
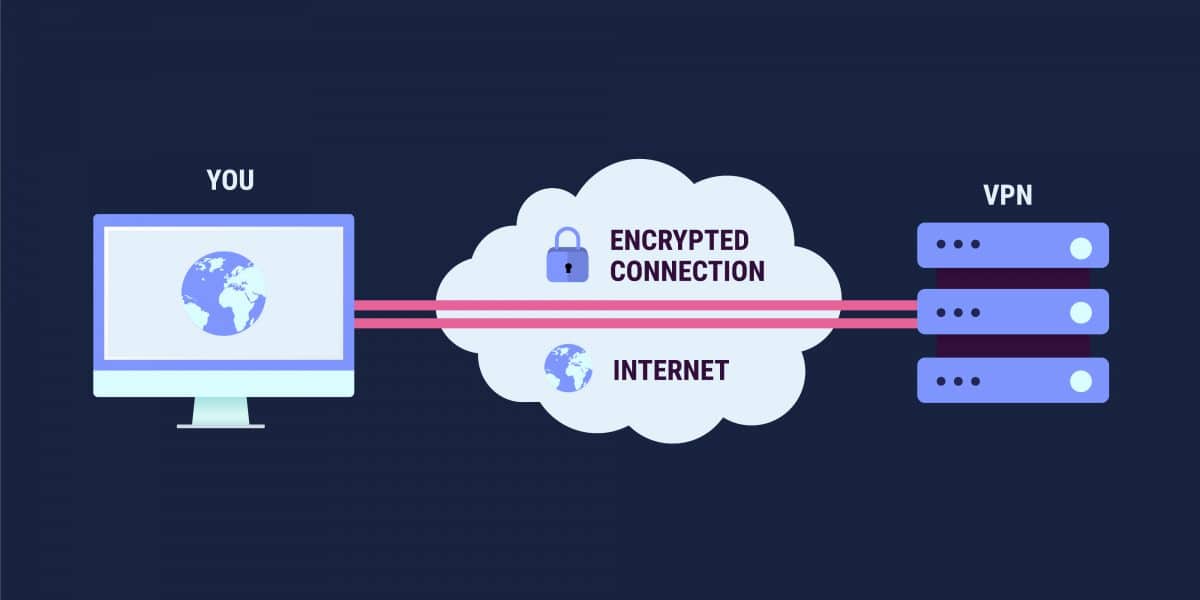
The internet is a series of interconnected networks. Each network is owned and run by other people, and the business owner with her LAN can’t control what goes on out on the other networks. Thus, a VPN is required. The VPN offers the same level of security that a company manager can impose on the private network. However, that security is provided through procedures and software, not guns, locks, and cable shielding – it is not physical privacy, it is virtual.
As with Tor, the main method of creating privacy is through encrypting all the information that travels across the internet, including the routing information. That routing information (with the addresses of the two computers that want to be in contact), is essential. It enables messages to be forwarded on from network to network, to reach each of the endpoints in the connection. VPNs solve this problem by having one computer mediate the contact between the two connected computers.
What Is Encapsulation?
When you connect your computer to another one across a network or the internet, it seems like a circuit has been closed, creating a temporary fixed link between your place and the cable that runs into the other computer. Once all the switches are in place to connect each segment of wire on the path, the two computers send a stream of data – particularly if you are watching a video over the web, where the data just flows constantly, like the water in a river.
In fact, you don’t have a path of cables just to yourself. Information travels along cables as an electronic pulse. When a charge is applied to the wire in the cable, it possesses all the length of the metal all at once. If that streaming service sent you a video as one long stream of electronic pulses, no one else along the route would be able to send an email or log into Facebook until you had finished watching the movie.
It wouldn’t be commercially viable, or physically possible, to run a separate cable to connect each two points on the internet. Thus, internet traffic has to run along shared cable. To prevent one customer locking out everyone else, each “connection” is broken up into little segments. Those segments have to travel across several different networks to get to their destination and then they all have to be reassembled. In order to manage that process, each segment has a header put onto the front of it that contains network routing information.
The exposure of the header information defines the difference between “security” and “privacy.” The segment of data in the payload of the packet may be encrypted so no one can read it. However, the header information is in plain text for all to read. Both Tor and VPNs use a method called “encapsulation” to obscure the information in the header.
Routers need to be able to see the destination address of a packet, otherwise they can’t pass it on. When Tor and VPNs encrypt the header information, they render that packet un-transportable. Therefore, the entirely encrypted packet is put in the payload of an outer packet. It is a little like those Russian matryoshka dolls, where a large doll figurine contains a smaller doll figurine, which in turn can be opened to reveal an even smaller doll.
What is Tunneling?
The privacy method that both Tor and VPNs use is called “tunneling.” This term provides a good analogy for the privacy offered by the system, because it does not create complete secrecy or total anonymity, but the identity of a connection is hidden from view for a section of its journey.
Tor encrypts all of your packets so the secret police can’t watch your traffic. However, how do you get to the start of the Tor protection? Once your packets leave the Tor network, how do you stop your traffic being seen on its way to its final destination?
In the case of VPNs, your packets are encapsulated between your computer and the VPN server. The server then strips off the outer packet and sends it on to its intended destination, giving its own IP address as the source. When the contacted computer responds, the VPN server remembers it was working for you and forwards the packet on, bundled up with encapsulation. But how does your computer know the encryption system it should use?
Client Software
With both Tor and VPNs, you need to download some software onto your computer in order to get to the tunnel.
With Tor, the client software on your computer calculates a route to take. The client calculates a route to pass through a randomly selected series of nodes.
The client takes each packet of a connection, encapsulates it, and puts the address of the endpoint on it. It then picks another node at random, encapsulates the packet and addresses it to that node. It then repeats that process several times. The resulting packet has many layers of encryption, like the layers of an onion.
The Tor-protected packet gets sent out like a Russian doll. The address on the outer packet delivers it to a private computer where the software strips off the outer layer, decrypts the inner packet, reads the destination address and sends it on. This process repeats until the exit node receives the last encapsulation. The packet is unbundled and sent on to its final destination.
In the case of VPNs, the client software encapsulates each packet that is about to leave your computer and sends it to its own home server. That server unbundles the packet and sends it on.
Anonymity with Tor and VPNs
Do Tor and VPNs give you total anonymity? No, they do not. You get privacy, but there is always a tiny problem with every security system, which creates a risk of failure. That flaw lies with the reliance on other people.
VPN Anonymity Problems
Not all VPNs are really as they seem. In January 2017, a study by the Commonwealth Scientific and Industrial Research Organization in Australia discovered that 18% of the 234 VPNs that they examined didn’t implement any encryption. Additionally, more than a third of the VPNs that they studied contained malware. Those services are like double agents: you get exposed to the authorities anyway.
Law firms of copyright holders are getting strident. They have been trying to shut down free download sites and prosecute torrenters. They force sites to reveal the identities of the people who visited them, and then they pursue those downloaders through the courts. They could just as easily go and lean on VPN companies to hand over all of their activity logs.
VPNs can give you security and privacy, but there is always the risk that if the VPN company knows who you are and what you are doing, it could either be coerced or bribed into passing on that information. This is why it is very important to research VPN companies before you subscribe to a service.
Make sure that the company is reputable and not a bunch of scammers trying to gain access to your computer. You also need to be sure that the VPN is actually doing what it says it is doing, and not just charging you for processing your traffic unencrypted. Finally, you should be certain that the VPN keeps no logs and that it is located in a country that has airtight privacy laws, so that the VPN doesn’t have any information to hand over to others.
Tor Weaknesses
The onion router was invented by the US Navy and, to this day, the Tor Project is largely funded by the US government. Hang on a minute! The National Security Agency (NSA), the US State Department and the Department of Defense have all gone on record praising the Tor Project as a wonderful thing. Why?
Most national security agencies regularly declare that Tor is completely un-crackable. However, the National Crime Agency in Britain managed to get into it during Operation Notarise in 2014. Also in 2014, Europol gloated publicly that it had managed to glean information during Operation Onymous through a Tor weakness. It refused to explain the flaw, saying,
This is something we want to keep for ourselves. The way we do this, we can’t share with the whole world, because we want to do it again and again and again.
The BBC reported in 2014 that the British police had found a technical weakness in Tor and now routinely accesses Tor traffic. The secret services of the US and the UK have an exceptionally close relationship. Tor was invented by the US military. Given these facts, it is highly likely that the UK police didn’t discover the exploit for Tor by themselves – they just gave the game away.
Further Problems with Tor
Who have we got building and maintaining this high-tech privacy system? Well, the military, the secret services, and the specialist police agencies of both the US and the UK use the system in-house. You can bet that they have very well-constructed privacy protection in place, which is run by the world’s top digital security experts.
The system available to the public is not so hot. It is maintained by volunteers, which means techie amateurs, fuming activists, paranoid conspiracy theorists, and others who have nothing better to do with their time.
Routing on the internet takes place on the fly. A router receiving a packet makes its own decision about where to send it on to, calculating the shortest, fastest route to the destination. With Tor, the originating computer pre-sets the route, so if one of the relay owners turns off her computer to go out to a demo, then the whole path collapses and the connection fails.
The Tor network doesn’t replace the internet, it travels over it. The random route is intended to just obscure the origin of a connection. However, Tor connections rarely continue right up to the destination. As such, there is a final segment of the route that is not covered by privacy protection.
As each node in the route is randomly selected, there is no guarantee that the exit note will be anywhere close to the destination computer. Thus, your traffic will end up travelling a lot of distance without any tunneling.
The random route of Tor makes sense for privacy, but it makes no sense at all from an efficiency standpoint. It could mean that if you want to access Netflix USA from Iran, your traffic first goes to Singapore then gets forwarded to Germany, follows on to Argentina and exits in Australia. It then has a long way to travel to get to the Netflix server in the US. Even then, you will be locked out by the geo-restriction methods of the streaming service, which only allows access from within the United States.
In order to get an exit node in the right country, you would have to keep cancelling the connection and retrying until you were randomly allocated an endpoint for Tor in the right place. You then have another problem to surmount. Tor drops and re-establishes connections via new random routes every ten minutes, at which point you will have to reconnect until you get the right location for the exit node.
Tor and VPN Comparison
Paid VPN services invest a lot in their infrastructure. A top-quality VPN company runs its own servers and even its own cable, which establishes super-fast, lightly-trafficked routes.
There is no standard of service for VPNs, so some are very technical and difficult to install, while others are extremely user-friendly and install themselves.
Streaming services impose access restrictions so that only people from within the same country can access video. They also realize that people use VPNs, so they work to block them. Some VPNs can get around these restrictions and others can’t. Those streaming services also block Tor traffic. Netflix and BBC iPlayer, for example, both log the IP addresses of discovered Tor exit nodes.
Tor’s random path makes its connections extremely slow, so you wouldn’t want to use it for online gaming. The unpredictability of its exit node selection means that this method of privacy is no good for streaming. Torrenting handshaking won’t work through Tor, so session establishment is unprotected and reveals your true IP address anyway.
Tor is very good at hiding the location of connection sources, so it is used by spies, victims of abuse, whistleblowers, and defense forces. It is very slow, so it is no good for most of the activities that the average person wants to get up to on the web.
Tor vs VPN Conclusions
Although VPNs offer better service than Tor to the general public, they can be expensive. Tor is free. Some VPNs are free to use, as well. However, look that gift horse in the mouth!
The reason reputable VPNs charge money for their service is because they invest a lot. Free VPNs may be scams, or useless hobbies constructed by amateurs. The involvement of volunteers in running Tor is also a worry.
Some people combine Tor with a VPN, but then, you just get the worst of both worlds – you will be slowing down your connection and every message will have to bounce around the world even more than when you just use Tor by itself.
If you are on the run from the FSB and want to contact The Guardian to tell your story, use Tor. If you want to download with torrents, stream video, or play online games, use a VPN – and be sure to check out reviews of VPNs before you commit!